This is part two of my RDP series on how to protect the communication, minimize the credentials exposure and how to use it in different delegation models.
This time we will have a look at an interesting delegation model using RDGW and RDP Restricted Admin mode.
I want to have a user dynamically/temporary member of an admin group. I don’t have JIT or JEA implemented so what can I do with built-in tools in the OS platform?
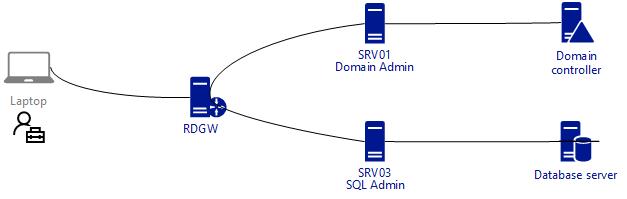
With RDPRA we have the possibilities to be a special admin depending on which server we jump to. It can look something like this:
In this example, we will grant a user Domain Admin rights temporarily, and in other cases he will just be a regular user.
In part one I wrote about RDPRA and how it flips the users identity to the servers identity he logon to. If a user RDP to a server with Restricted Admin mode, he will thru that machine connect to other resources in that context. If we make that server a member of Domain Admins the user will become a Domain Admin only by landing on that machine, and it happens automatically only thru RDP.
So, we start with stealing the setup from part one and add the server to Domain Admins group. Now when my user Tony connects to the server he is effectively a Domain Admin.
Sure, we need to step up our game on logging and correlations of event logs to get a clear picture of who did what. This isn’t about Auditing, so I will save that for some other time. Continue reading