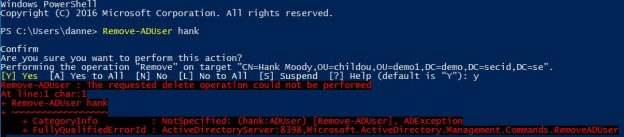
What is required to delete admin accounts that is member of a protected group like Domain Admins or Enterprise Admins?
The most common answer is whoever has the Delete Right on the user object. But when it comes to ACLs in Active Directory it’s not always that easy. ACLs is a powerful and complex thing in Active Directory.
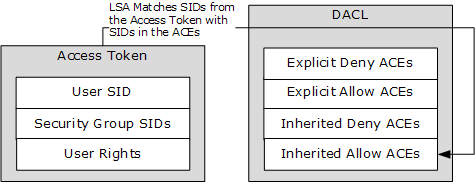
If we read the Microsoft documentation on how the system evaluates if a Security Principal is allowed and denied access: Discretionary Access Control Lists (DACLs) and Access Control Entries (ACEs)
When access is requested to an Active Directory object, the Local Security Authority (LSA) compares the access token of the account that is requesting access to the object to the DACL. The security subsystem checks the object’s DACL, looking for ACEs that apply to the user and group SIDs referenced in the user’s access token. The security subsystem then steps through the DACL until it finds any ACEs that allow or deny access to the user or to one of the user’s groups. The subsystem does this by first examining ACEs that have been explicitly assigned to the object and then examining ones that have been inherited by the object. The following illustration shows the important parts of an access token and a DACL when a request is evaluated.
If an explicit deny is found, access is denied. Explicit deny ACEs are always applied, even if conflicting allow ACEs exist. Explicit allow ACEs are examined, as are inherited deny and allow ACEs. The ACEs that apply to the user are accumulated. Inherited deny ACEs overrule inherited allow ACEs but are overruled themselves by explicit allow permissions. If none of the user SIDs or group SIDs in the access token match the DACL, the user is denied access implicitly.
Now to the fun part, when talking about deletion you must consider a little more than just this logic to determine the effective permissions granting a user to delete a Domain Admin user. Continue reading