This is just a small note of a feature that was new in Windows 10 v1507 and Windows Server 2016.
In the early days (Windows 2000, XP and 2003) it was possible to configure Service Principals Names (SPNs) with IP addresses. And then in Windows Vista and Windows Server 2008 it was removed in the Kerberos client and IP addresses on services didn’t work.
Since then if a client tries to connect to e.g. a share by its IP address it would fall back to NTLM.
I don’t know why that changed, but the good news is that they have reintroduced that functionality and you can configure the Kerberos clients to request a service ticket based on a IP hostname SPN.
The client needs to be configured with a new DWORD: TryIPSPN with the value 1. Default it isn’t there and the client will fall back to NTLM.
Either you create it with Group Policy or you can use the command line:
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters /v TryIPSPN /d 1 /t REG_DWORD
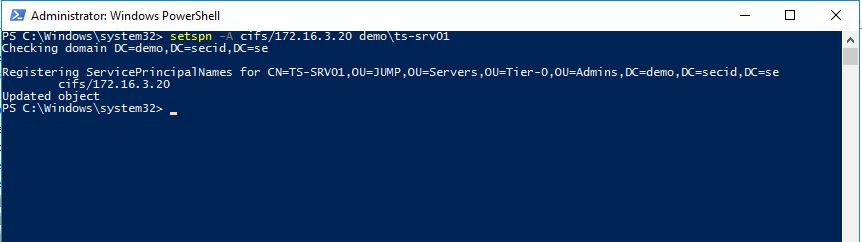
And of course, you need to register the SPN on a service. In this case we will use a share as an example on my server ts-srv01:
setspn -A cifs/172.16.3.20 demo\ts-srv01
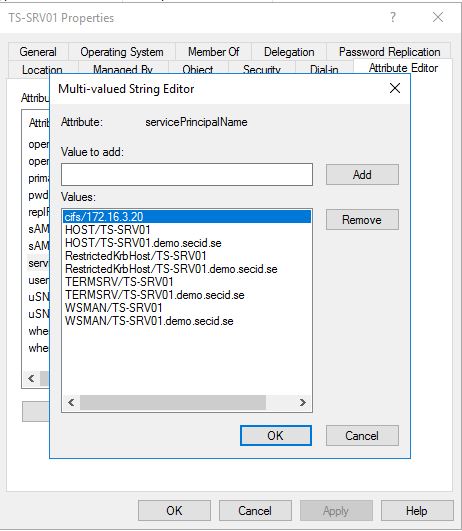
We can verify it in the servicePrincipalName attribute on the server object:
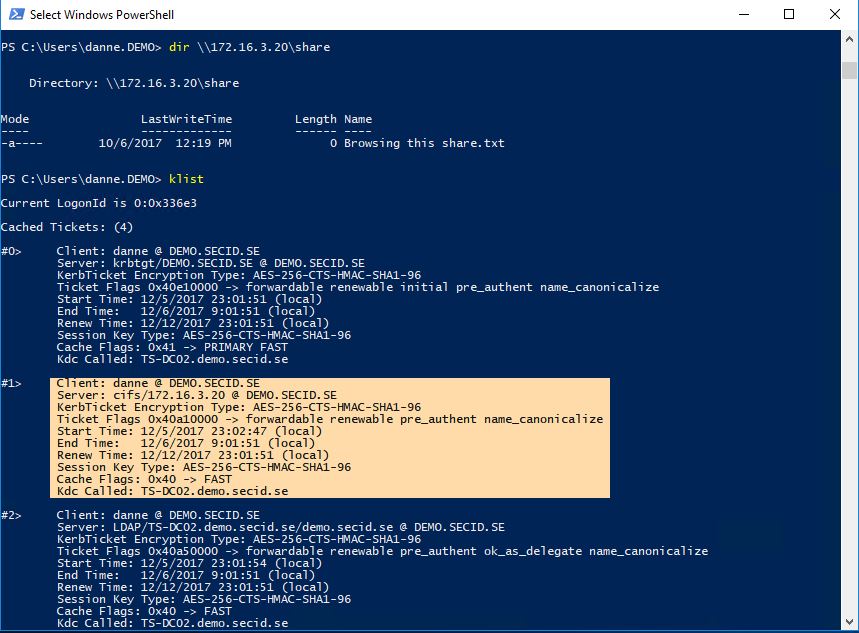
And now if we test to browse that share on the IP we can see that we got a Kerberos Service Ticket based on the IP address.
This is a client-side feature and isn’t dependent on any Forest or Domain Functional Level, OS version on Domain Controllers or server/services. It’s also supported for IPv6, quite nice.
With this we can use Kerberos in more places and minimize the usage of NTLM a little bit more.