I got a question about LAPS and deleted Computer objects.
What happens if a Computer is disjoined from the domain or if the object is deleted, how do we recover the LAPS password?
And for how long can we recover the LAPS password? (if we don’t look at the backups you should have).
Computer is disjoined:
If you configure the client to join another Domain or a Workgroup the Computer object isn’t deleted in the Active Directory database. At most the computer account is disabled. No problems retrieving the password there.
Computer Object is deleted in the Active Directory database:
This depends on what you have configured.
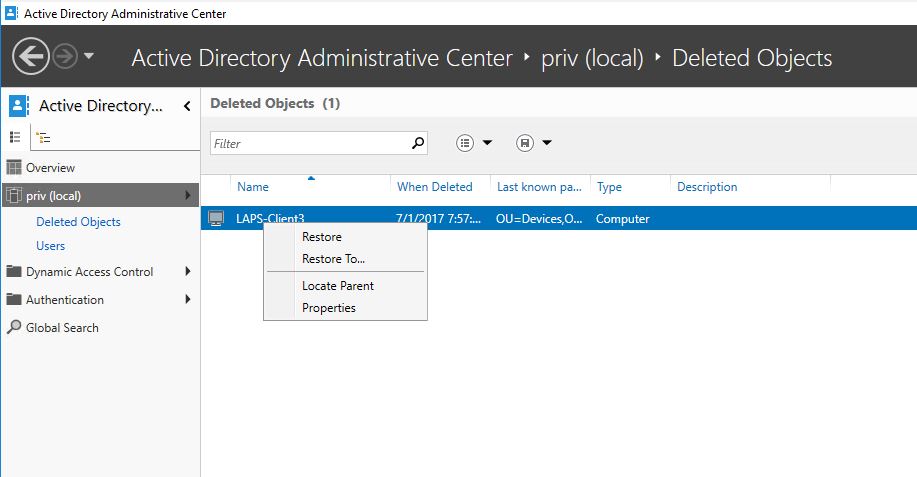
Hopefully you have the optional feature Active Directory Recycle Bin enabled and you can restore the object with PowerShell or by using the Active Directory Administrative Center tool if you want a GUI and has Windows Server 2012 DCs or RSAT.
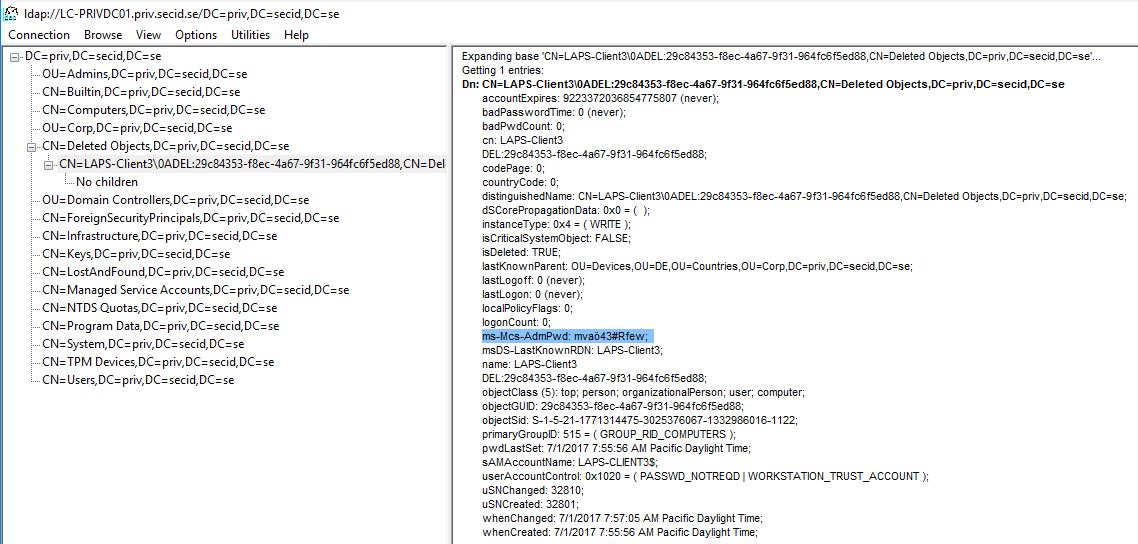
If you only want to retrieve the password without restoring the object you can see the computer object and its attributes in the “CN=Deleted Objects” container in the Domain Naming Context. Note: Its only default visible in the 2012 ADAC tool if you have AD Recycle Bin enabled.
Let’s say that you have DCs no older than Windows Server 2008 R2 and has Recycle Bin enabled:
When a computer is deleted its moved to the Deleted Objects container in its corresponding NC and the attribute isDeleted is set to TRUE.
The object becomes Logically Deleted and all link-valued and non-link-valued attributes of the deleted object are preserved. and with PowerShell or LDP we can still retrieve the attribute values.
PowerShell:
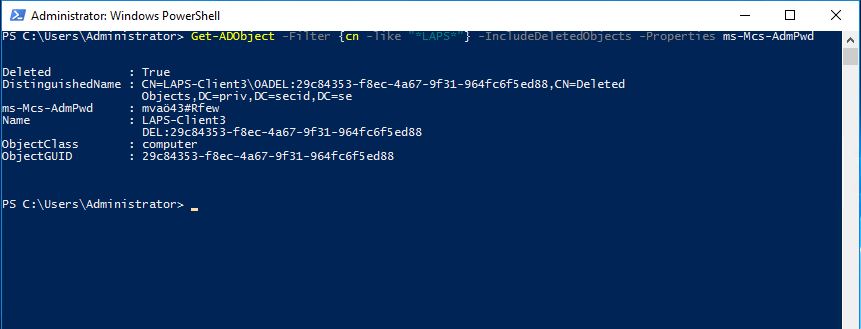
With the Get-Adobject cmdlet we can find the deleted objects and retrieve the value of ms-Mcs-AdmPwd attribute.
LDP:
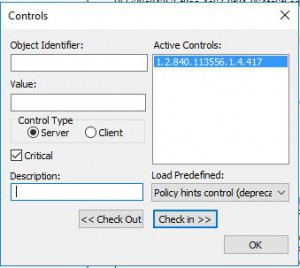
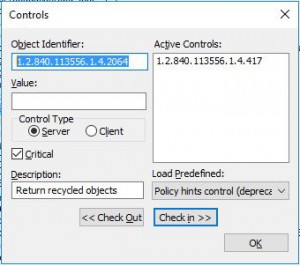
Load the LDAP Control “Return deleted objects:1.2.840.113556.1.4.417”
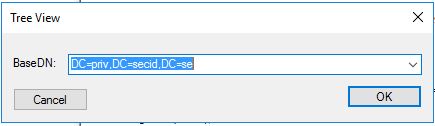
Choose View – Tree and DNC as your BaseDN.
Browse to the CN=Deleted Objects,DC=X and you can retrieve the ms-Mcs-AdmPwd value of the desired computer object.
The amount of time the object is stored as isDeleted is controlled by the attribute msDS-deletedObjectLifetime and is stored in the “CN=Directory Service,CN=Windows NT, CN=Services, CN=Configuration, DC=X” container. Default its 60 – 180 days depending on the Tombstone lifetime.
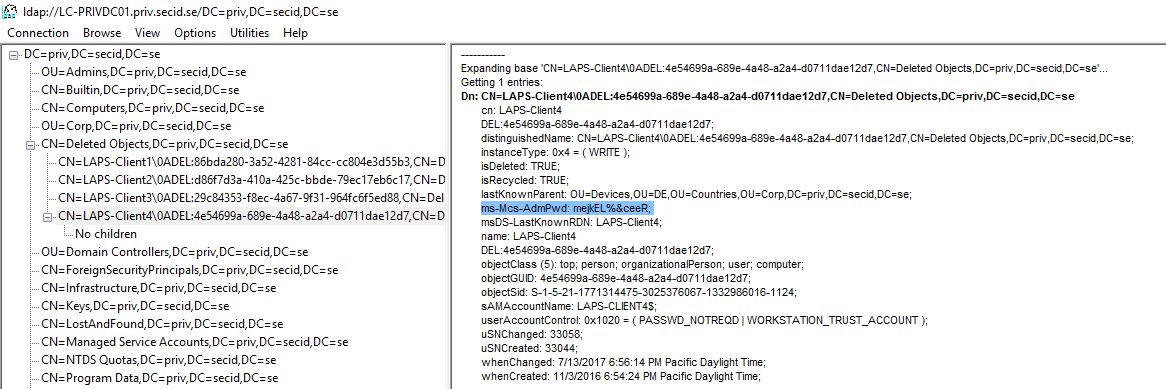
During this time the object can be restored. When the Deleted Object Lifetime has exceeded, the objects attribute isRecycled is set to True and the object is tombstoned and striped of attribute values. It is still stored in the Deleted Objects container during the tombstone lifetime.
Note: List of preserved attributes in tombstone objects see: Reanimating Active Directory Tombstone Objects
The tombstone lifetime (or recycled object lifetime) is 60-180 days depending of which OS version the forest was built on and if the tombstoneLifetime attribute has a value or if its null or not set. If it’s built on Windows Server 2003 SP1 and newer the value is set to 180 days. The attribute is stored in the “CN=Directory Service,CN=Windows NT, CN=Services, CN=Configuration, DC=X” container.
When the object is tombstoned/Recycled it is no longer restorable and it misses a lot of valuable information since it was stripped of a lot of its attribute data. The only purpose now is to let the DCs know the object is gone and when the tombstone lifetime exceeds it will be physically deleted by Garbage Collection.
Note: When AD Recycle Bin is enabled tombstone reanimation nor Restore-ADObject cmdlet is not supported on tombstoned objects. When AD Recycle Bin isn’t enabled, even though the object has isDeleted and isRecycled tombstone reanimation and Restore-ADObject is supported.
And here is the last stop for recovering LAPS passwords. The ms-Mcs-AdmPwd attribute has the searchFlags 8 bit PRESERVE_ON_DELETE. This means that when the computer object is tombstoned/Recycled the ms-Mcs-AdmPwd attribute value is preserved.
And with e.g. LDP we can still retrieve it by loading the LDAP Control “Return recycled objects: 1.2.840.113556.1.4.2064”
I deleted my LAPS-Client4 computer object and fast forwarded to July 2017 and triggered the DoGarbageCollection operational attribute. And now we can see the tombstoned object with less attribute values but the ms-Mcs-AdmPwd is preserved.
When using AD Recycle Bin the LAPS password can be retrieved by the time of Deleted Object Lifetime and the Tombstone lifetime which normally is 180 + 180 days which is probably more than you will need.
If you don’t have AD Recycle Bin enabled, you have the time of tombstone lifetime to recover the password.
Bonus:
If you need to delegate a special set of users to being able to recover the password:
Since the Security Descriptor is preserved and still used all the way to tombstoned object (no inheritance involved from the Deleted Objects container), the already delegated LAPS admins can still see the password. All they need is List Contents and Read Property on the Deleted Objects container. Either you leave it that or have a special group for LAPS password recovery.
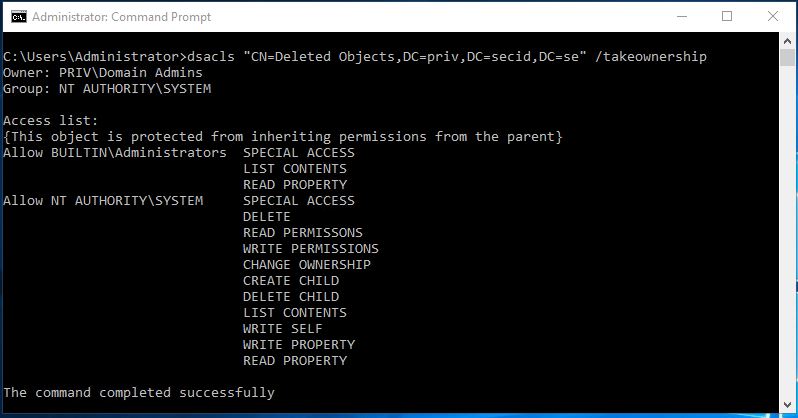
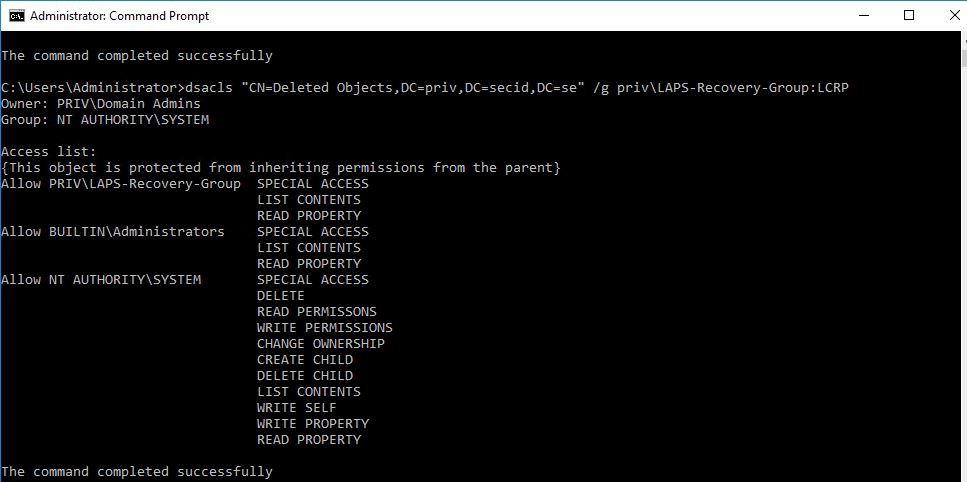
You could use DSACLS to delegate the permissions to the LAPS-Recovery-Group.
First logon with a Domain Admin account and take ownership of the object CN=Deleted Objects,DC=X with the DSACLS tool:
Set the List Contents and Read Property permissions for the group you want to delegate this to:
And now you have some admins that can read the Deleted Objects container and retrieve the LAPS password (if they were allowed to read the LAPS password before deletion).