This is a simple guide delegating DHCP Admins in the domain.
This guide is built on a Windows Server 2012R2 environment.
If you have a lot of DHCP servers and want to delegate the administration in your domain it’s quite easy, and a good thing to do if you don’t want to grant people Domain Admin access unnecessarily. But, there is a few differences you need to know depending on How and Where you install the DHCP Server Role.
If we start with the most common way installing the DHCP Server Role service which is an easy task.
PowerShell:
Add-WindowsFeature -IncludeManagementTools dhcp
-Done 🙂
When installed start the DHCP MMC snap-in (or just continue to use PowerShell) and configure your scopes and options, authorize the DHCP server and everything works well. Yeah, if you are a Domain Admin!
Personally I don’t like to use DA when not needed and it’s not uncommon the DHCP Server role is hosted on Domain Controllers. But what if I don’t want the DHCP admin who performs the daily tasks to be a Domain Admin nor even a local Administrator on any DHCP server and the management server?
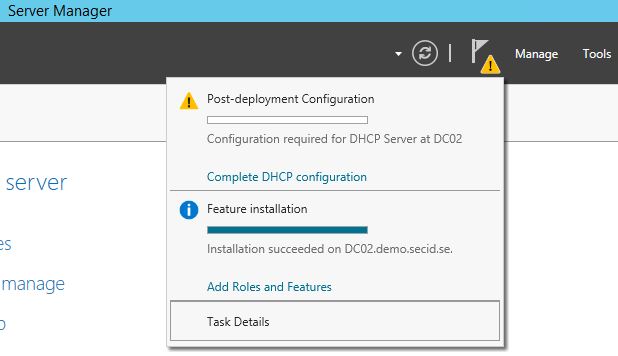
In Active Directory there is no default built-in DHCP Administrators group at domain creation with a well-known SID\RID. But there is a step in the DHCP installation process I didn’t cover and it’s not unusual people missed it.
After installing the DHCP Server role we need to perform a post deployment configuration which people don’t always notice.
If you run it:
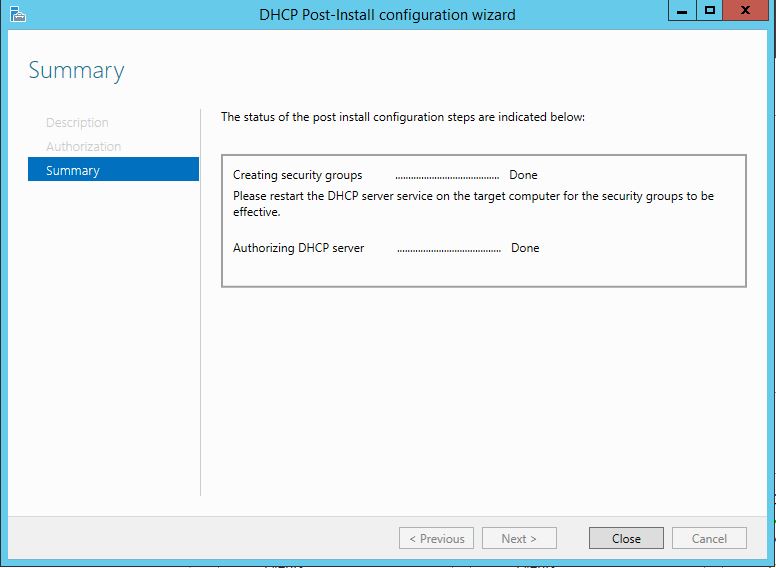
This will create two new groups and set the right permissions for the DHCP service:
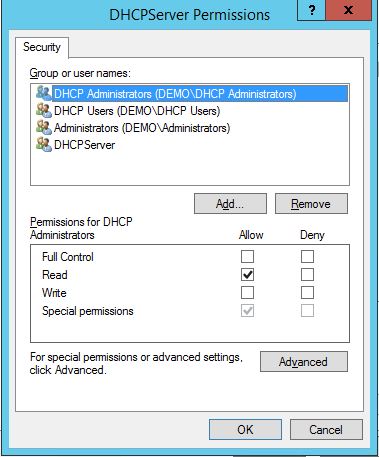
DHCP Administrators
DHCP Users
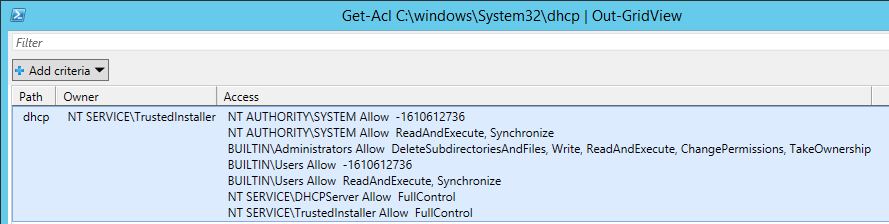
Since 2008R2 the DHCP service runs default under the NT Service\DHCPServer context. In the DHCP folder where the database file resides we can see the ACLs.
During post configuration permissions is set to manage the Service and not directly on the folder and in the registry.
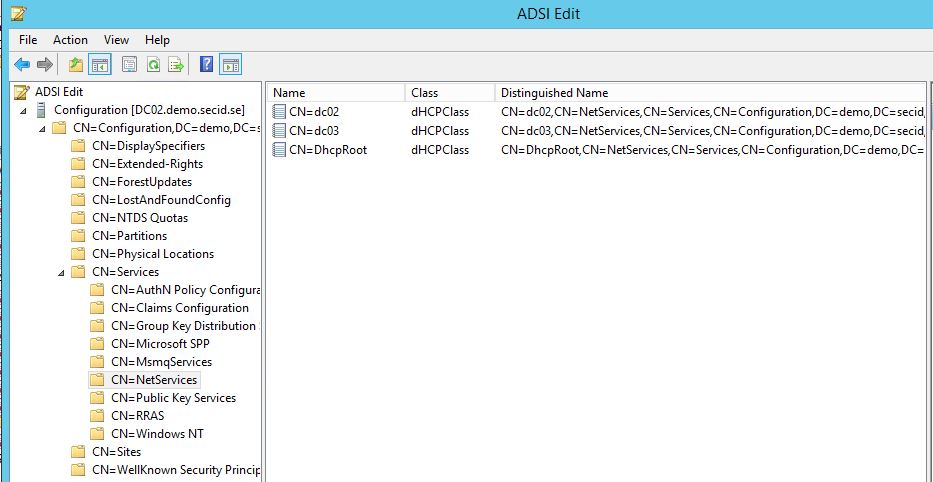
The second thing that is done is Authorization of the DHCP server in the domain. When authorized it’s allowed to start serving IP leases. The authorization data is stored in the NetServices container in the Configuration Naming Context.
How do we take advantage of this information and use it in a proper manor?
Create a new DHCP Admins group where your delegated users will be members of.
New-ADGroup -Name “Role-DHCP-Admins” -DisplayName “Role-DHCP-Admins” -Description “Members allowed to manage DHCP Servers” -GroupCategory Security -GroupScope Universal -Path ” OU=On-Prem,OU=Roles,OU=Tier-1,OU=Admins,DC=demo,DC=secid,DC=se ”
If we liked to, we can also pre-stage the DHCP groups in AD and let them replicate to all DCs before installing the DHCP service.
New-ADGroup -Name “DHCP Administrators” -DisplayName “DHCP Administrators” -Description “Members who have administrative access to the DHCP Service” -GroupCategory Security -GroupScope DomainLocal -Path “OU=On-Prem,OU=Security,OU=Tier-1,OU=Admins,DC=demo,DC=secid,DC=se”
New-ADGroup -Name “DHCP Users” -DisplayName “DHCP Users” -Description “Members who have view-only access to the DHCP service” -GroupCategory Security -GroupScope DomainLocal -Path “OU=On-Prem,OU=Security,OU=Tier-1,OU=Admins,DC=demo,DC=secid,DC=se”
NOTE: If you already installed the DHCP server service on a DC and ran the post deployment configuration the groups should already exist in your AD. Default in the Users container if you haven’t redirected it with redirusr.exe
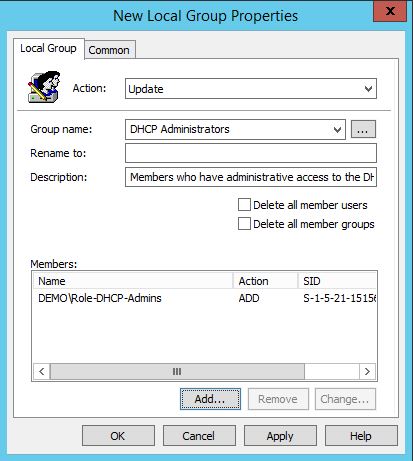
Make the role group “Role-DHCP-Admins” member of the DHCP Administrators group.
Now it’s time for delegation in AD.
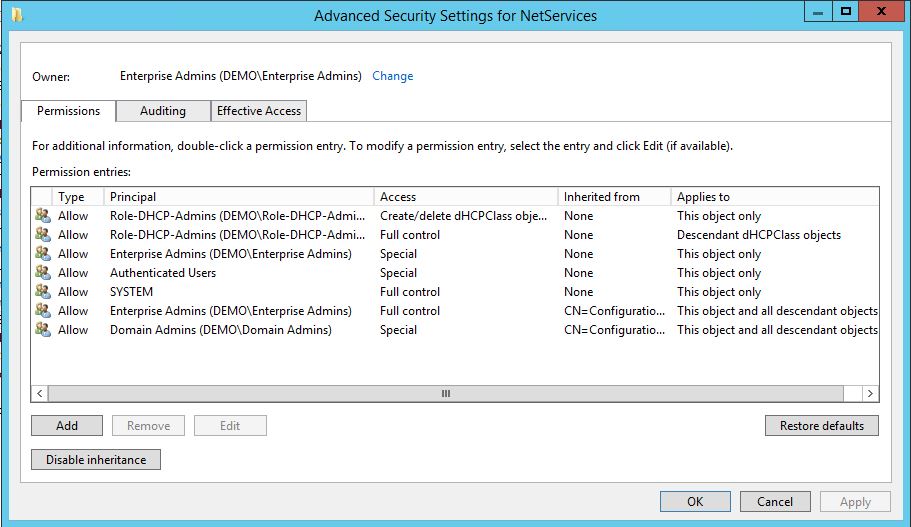
Open ADSI Edit and connect to the Configuration Naming Context.
Open properties for the container: CN=NetServices,CN=Services,CN=Configuration,DC=demo,DC=secid,DC=se in the security tab choose Advanced and then Add.
Select the security principal Role-DHCP-Admins and on the object grant Create/Delete dHCPClass objects.
Grant Full Control on descendant dHCPClass objects.
Now were ready to install the DHCP Server Service on a DC. When done, runt the command: Add-DhcpServerSecurityGroup or netsh.exe dhcp add securitygroups on the DC and the appropriate permissions will be set for the DHCP Administrators and Users groups.
NOTE: This needs to be done on every DC you install the DHCP Server Role on, granting the groups to manage the service.
If you install the DHCP Server Role on a member server the groups will be created as local groups and we can use Group Policy Preferences or Group Policy Restricted Groups to make the Role-DHCP-Admins group a member.
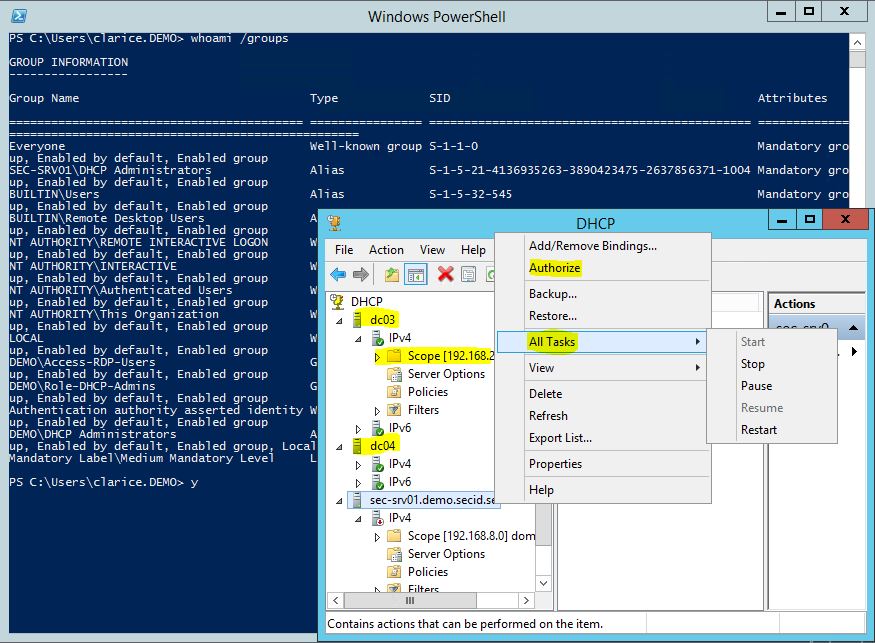
Now the delegated DHCP users won’t need to be a Domain Admins nor local Administrator anywhere. Success!
And if you only want users to be able to read the DHCP configuration, create a read users role and add them to the DHCP Users group.
Summarizing:
- Create delegated Role-DHCP-Admins group (One time only on in AD).
- Pre-create DHCP Administrators and Users groups (Optional).
- Add Role-DHCP-Admins group as member in DHCP Administrators.
- Delegate permissions for dHCP Object Class in the NetServices container.
- Now the delegated users can take it from here. Working from a management server, create scopes, configure options, authorize the server and restart the DHCP service.
Bonus:
If you want to disable the notification of post config in Server Manager run this PS command:
Set-ItemProperty –Path registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ServerManager\Roles\12 –Name ConfigurationState –Value 2
You should also take a look at securing the DNSupdateproxy group:
https://technet.microsoft.com/en-us/library/ff631099(v=ws.10).aspx
Another good blog about, DHCP and DNS:
http://blogs.msmvps.com/acefekay/2009/08/20/dhcp-dynamic-dns-updates-scavenging-static-entries-amp-timestamps-and-the-dnsproxyupdate-group/
Thank you, this is the first REAL and great solution for this issue.
Does the “Role Admin” group have to be Universal or can it be Global? I run my DHCP on a member server that, so based on your article, I should just ad my AD group to the local DHCP admins on the member server and they will be able to admin. We have been trying to give them access to manage DHCP, but not allow them access to the server using the MMC on the workstation, without a lot of luck. I am going to revisit it today. Our systems are crazy hardened, so I suspect that is our more likely cause for the issue we have. Thanks.
No it dont.