Got a question a couple of days ago about how to install the Active Directory PowerShell module on a machine that doesn’t have the ADDS role. That’s pretty basic, but in some cases there could be some better options so I decided to write a post.
I will start with a short walkthrough of installting RSAT and then go in to PowerShell Remoting.
If you want the AD PowerShell cmdlets on your local PC or maybe a management server you only have to install Remote Server Administration Tools (RSAT). RSAT is a collection of remote management tools for the Windows Server Operating System.
For the clients it can be downloaded from Microsoft:
Win 7 SP1:
http://www.microsoft.com/en-us/download/details.aspx?id=7887
Win 8:
http://www.microsoft.com/en-us/download/details.aspx?id=28972
Win 8.1
http://www.microsoft.com/en-us/download/details.aspx?id=39296
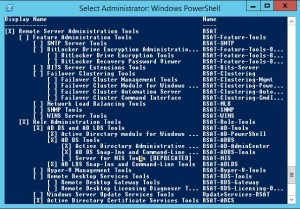
After it is installed you have to open Programs and Features in Control Panel and choose Turn Windows Features on or off.
Navigate to Remote Server Administration Tools\Role Administration Tools\AD DS and AD LDS Tools\ and check the Active Directory Module for Windows PowerShell.
Or you could use the old boring command line CMD: dism /Online /Enable-Feature /FeatureName:RemoteServerAdministrationTools-Roles-AD-Powershell
For Windows Servers RSAT comes with the OS.
You could add it by using the Add Roles and Features guide in Server Manager but since this is a PowerShell post we will use it as much as possible.
In PowerShell 3.0 (Default in 2012 server and Win 8) there is a new feature Auto-Loading which automatic scan all modules in the default path for commands and loads the module for a specific cmdlet. If you haven’t upgraded PowerShell on your 2008R2 you first have to import the module Servermanager.
Start with:
Import-Module Servermanager
Since we are only interested in RSAT we can use:
Get-WindowsFeature *RSAT*
And you will see a list of all the RSAT tools.
In this case we are interested in RSAT-AD-PowerShell tool.
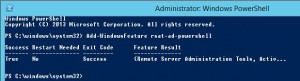
Add-WindowsFeature RSAT-AD-PowerShell
If you want to add multiple tools you can use comma to separate the tool names.
Add-WindowsFeature RSAT-AD-PowerShell,RSAT-ADCS,RSAT-DNS-Server
And at last if you want to add all the tools you simply run:
Add-WindowsFeature RSAT
And now to the second and more interesting part.
If you don’t have RSAT installed, or if you want to execute a script or command remote on one or more severs. How do you do that? PowerShell Remoting of course!
If we start with the remoting without any configuration. Many cmdlets have a –ComputerName parameter which makes it possible to collect data and configure one or more remote computers without not having to do any special configuration on the computer or server.
A few examples:
Restart-Computer
Test-Connection
Clear-EventLog
Get-EventLog
Get-Hotfix
Get-Process
Get-Service
Get-Service
Get-WinEvent
Get-WmiObject
If you want to list all cmdlets with that option, simply run:
get-command | where { $_.parameters.keys -contains “ComputerName” -and $_.parameters.keys -notcontains “Session”}
And now to the coolest…
Windows PowerShell Remoting.
Windows PS-Remoting uses the WS-Management Protocol which is a DMTF open standard defining a SOAP-based protocol for the management of servers, devices, applications and various Web services.
WS-Management is part of the Windows Remote Management (WinRM). WinRM is a modern tool that enables you to remotely manage and execute programs on Windows computers.
It uses the HTTP and HTTPS which makes it easy to manage in the firewalls. And don’t worry for using HTTP, the authentication is still encrypted using Integrated Windows Authentication (IWA), but if you want to encrypt the whole session and have an internal PKI, I would suggest to distribute server certificates and enable SSL.
(Note. WinRM 1.0 used the default ports for HTTP 80 and HTTPS 443 but was changed in WinRM 2.0 to use transport HTTP on port 5985 and HTTPS on port 5986.
There are many ways to enable PS-Remoting. In Windows 2012 Server it is enabled by default. But if it’s not activated you can use a couple of commands.
- Winrm quickconfig – Enables WinRM with default options.
- Enable-PSRemoting -force – Runs the Set-WSManQuickConfig cmdlet.
- Set-WSManQuickConfig – Runs the following tasks:
‒ Starts the WinRM service.
‒ Sets the startup type on the WinRM service to Automatic.
‒ Creates a listener to accept requests on any IP address.
‒ Enables a firewall exception for WS-Management communications.
‒ Registers the Microsoft.PowerShell and Microsoft.PowerShell.Workflow session configurations, if they are not already registered.
‒ Registers the Microsoft.PowerShell32 session configuration on 64-bit computers, if it is not already registered.
‒ Enables all session configurations.
‒ Changes the security descriptor of all session configurations to allow remote access.
‒ Restarts the WinRM service to make the preceding changes effective.
On the client side you don’t need to do anything but fire up PowerShell.
One last way to enable PS-Remoting which I prefer in some cases, is by using Group Policy.
Open GPMC and create a new Group Policy Object. Edit it and browse to: Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Remote Management (WinRM)\WinRM Service\
Enable the Allow remote server management through WinRM policy. There are a few other policys you should take in to considerations depending on your requirements. Close the editor and link the policy to the OU containing the server you want this enabled on.
(Note. If you enable WinRM thru GPO you also need to open FW ports on the servers. This can also be done with GPO or manually)
Now to test this you can use the Test-WSMan cmdlet.
Test-WSMan -ComputerName srv001
Now when we finally has this enabled and working. I will use two great cmdlets.
1. Invoke-Command
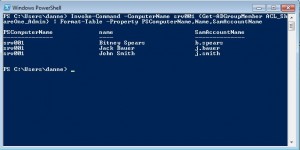
You can use the Invoke-Command cmdlet to run a command on a remote computer. For example if I want to query the members in an AD group and don’t have the AD module I could run:
Invoke-Command -ComputerName srv001 -scriptblock {Get-ADGroupMember ACL_ShareOne_Admin} | Format-Table -Property PSComputerName,Name,SamAccountName
And you get a well formatted list of the server that was run against and the members of the group.
2. Enter-PSSession
Starts an interactive session with a remote computer and it would be like working directly on the server.
Enter-PSSession –ComputerName srv001
There are a lot of ways to mix this cmdlets together and a lot of others.
To learn more:
http://msdn.microsoft.com/en-us/library/aa384426(v=vs.85).aspx
http://technet.microsoft.com/en-us/library/hh849719.aspx
http://technet.microsoft.com/en-us/library/dd819505.aspx
http://technet.microsoft.com/en-us/library/hh849707.aspx
http://technet.microsoft.com/en-us/library/hh849717.aspx
http://technet.microsoft.com/en-us/library/hh849719.aspx